Securing your Leanplum API keys
Leanplum uses client keys for authentication when using the API. Authentication is done by adding the clientKey and appId parameters to the HTTP requests. All data is encrypted in transit over TLS and HTTPS.
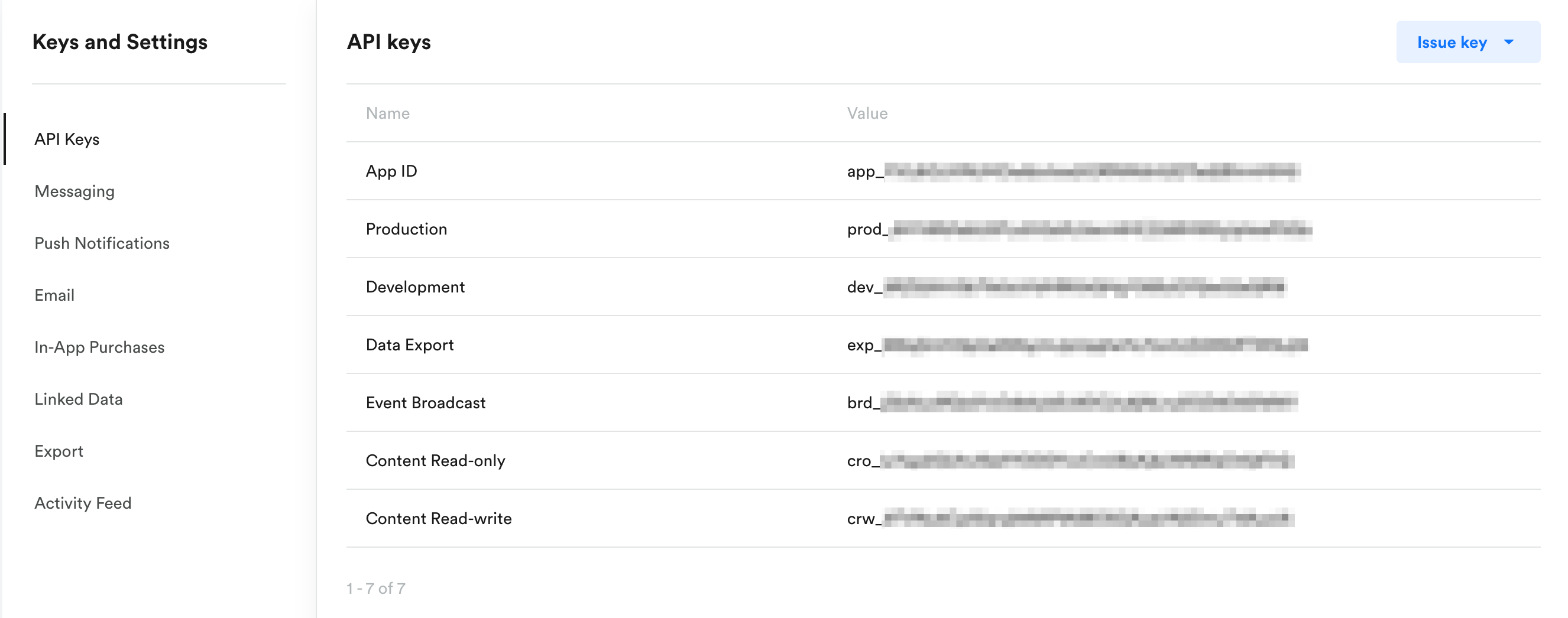
Your keys are located in App Settings in the Leanplum dashboard.
Using the right keys
Each app has a set of keys, and each key has different permissions associated with it. For example, you'll see a Production key, a Development key, a Data Export key, etc.
- Use a Production key in a live, production app — it contains the most limited set of permissions and is meant to be used when sending production data to Leanplum.
- Use a Development key only in tightly-controlled development environments (Staging / QA). It has a higher level of permissions associated with it and must never be used to send production traffic to Leanplum.
Use only Production keys when you bundle/ship an app, accessed by users. See Using the right API keys for more information on when to use a production key versus a development key.
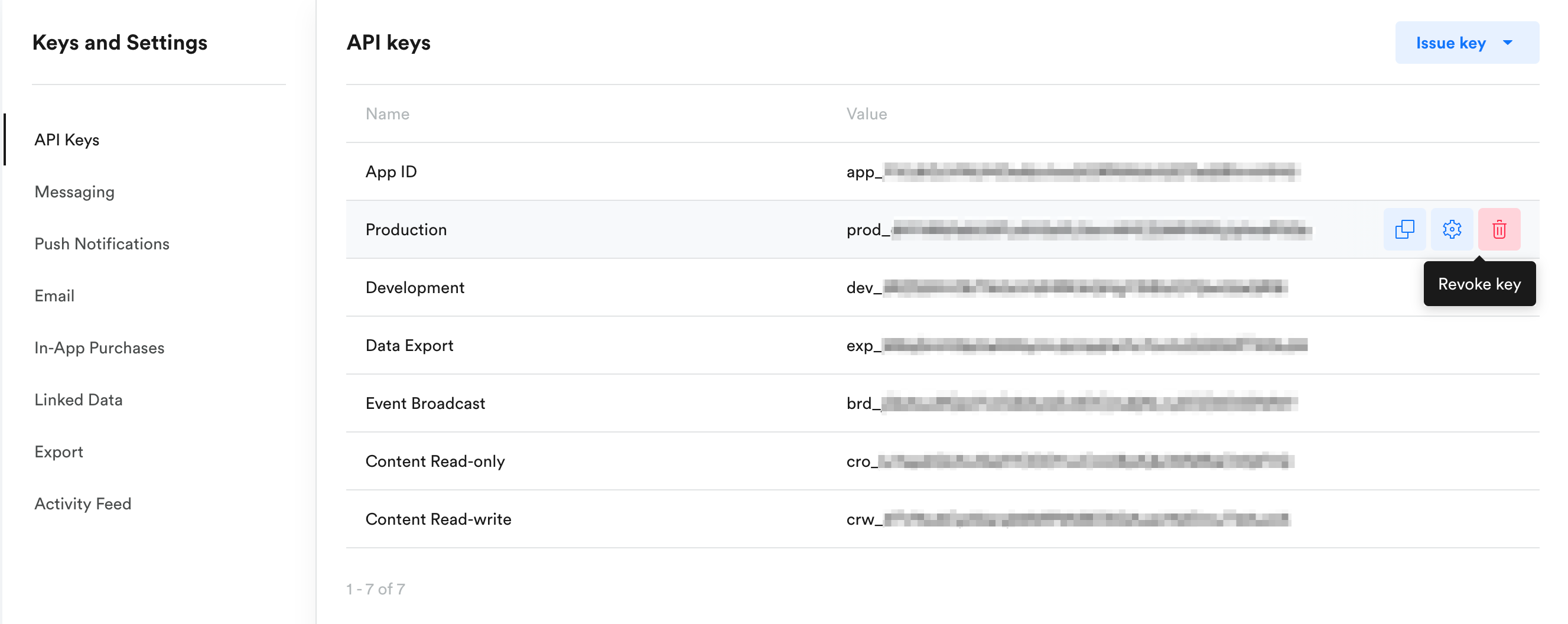
Reissue keys
If you suspect that a malicious third party has obtained access to one of your keys, you can deactivate that key and issue a new one. To start tracking, you need to update your apps with the new key. You can do this in App Settings under Keys & Settings.
Updated 6 months ago
